The Challenges of Hybridization in the Modern Workplace: Perspectives and Strategies
The Emergence of Hybridization Hybridization of IT infrastructures is a major challenge for businesses, whether they are small or large....

The question of local administrators is one that arises quickly when discussing a digital transformation from a technical perspective. Local administrators are primarily used for support purposes.
As this topic is primarily managed through Group Policy Objects (GPO), how can it be best translated into Intune? How can local administrators be granted privileges on devices joined to Azure AD and detached from Active Directory?
Since the update to version 20H2 of Windows 10, it has become possible to effectively manage local administrators through a configuration created in Intune.
By creating a customized configuration, here is what it looks like: OMA-URI: ./Device/Vendor/MSFT/Policy/Config/LocalUsersAndGroups/Configure
Datatype : String
Value :
<GroupConfiguration>
<accessgroup desc = “Administrators”>
<group action = “U” />
<add member = “S-1-12-1-2467210666-1203319661-2805276081-2339455698″/>
<add member = “AzureAD\
us***@sy**********.com
“/>
<remove member= “Tom”/>
</accessgroup>
</GroupConfiguration>
In this context, the action “U” means that we are going to “Update” the local Administrators group by adding and/or removing members.
It is also possible to use the action “R,” which will “Replace” (Restrict) all local users of a group with those you list in the configuration.
Note that in this example configuration, various targets are managed:
This configuration can be targeted to a group of devices, varying in size.
Indeed, in international contexts where a team of administrators manages a country, one can imagine a configuration per country deployed to the Azure AD device group of that country.
When a device is joined to Azure AD, two SIDs are systematically added to the SAM database. These are the SIDs of the two Azure AD roles, Global Administrator and Device Administrator.
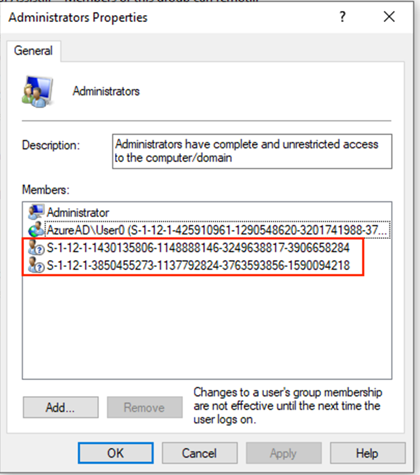
This means that anyone with these two roles is, by default, an administrator of the devices. One solution may be to assign these two roles to the desired admins.
However, this solution, while native to Azure AD, implies that administrators assigned to the Device Administrator role are administrators of ALL devices in the directory. This model may be suitable for smaller contexts, but when it comes to real detailed delegation, it will encounter security limitations.
If you choose the first method, removing these two SIDs may be relevant.
Whether through an approach allowing delegation or a native Azure AD approach, managing local admins is a question that Modern Management can address. Doing so through Intune or Azure AD allows addressing this issue for devices in a workgroup, for example, that were previously unaffected by GPOs. We now have centralized management of local admins for all devices!
Articles Similaires
The Emergence of Hybridization Hybridization of IT infrastructures is a major challenge for businesses, whether they are small or large....
The definition of roles and scopes in IT tools is a central issue in a modern workplace project. Due to...
Personal devices in the workplace are common, with many employees, both internal and external, preferring to use their own devices...